Revolutionizing Crypto Security with AI-Powered Threat Detection
Our advanced protocol leverages machine learning and blockchain analytics to identify and neutralize crypto threats in real-time, ensuring your digital assets remain protected against sophisticated attacks.
Table of Contents
Why Choose Our Crypto Security Platform
Comprehensive Crypto Protection Suite for Modern Blockchain Ecosystems
We provide end-to-end security solutions designed specifically for cryptocurrency projects, exchanges, and institutional investors.
Smart Contract Protection
Advanced vulnerability scanning and real-time monitoring for DeFi protocols and smart contracts across multiple blockchain networks.
Exchange Security
Enterprise-grade security for cryptocurrency exchanges including cold storage management, withdrawal protection, and API security.
Wallet Protection
Multi-signature solutions, biometric authentication, and hardware wallet integration for maximum asset security.
Multi-Layered Defense System for Maximum Crypto Protection

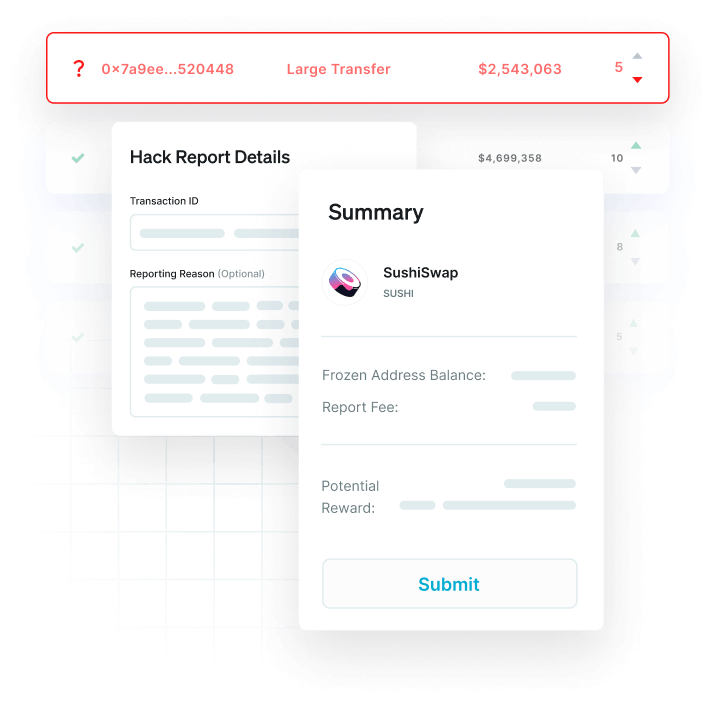
Proactive Threat Detection
AI-powered algorithms continuously monitor blockchain activity, identifying suspicious patterns and potential threats before they materialize into attacks.
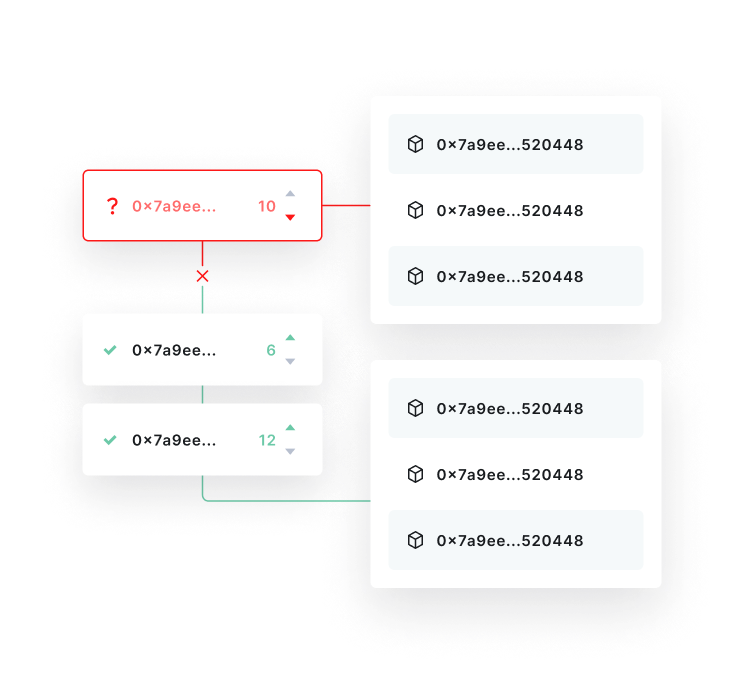
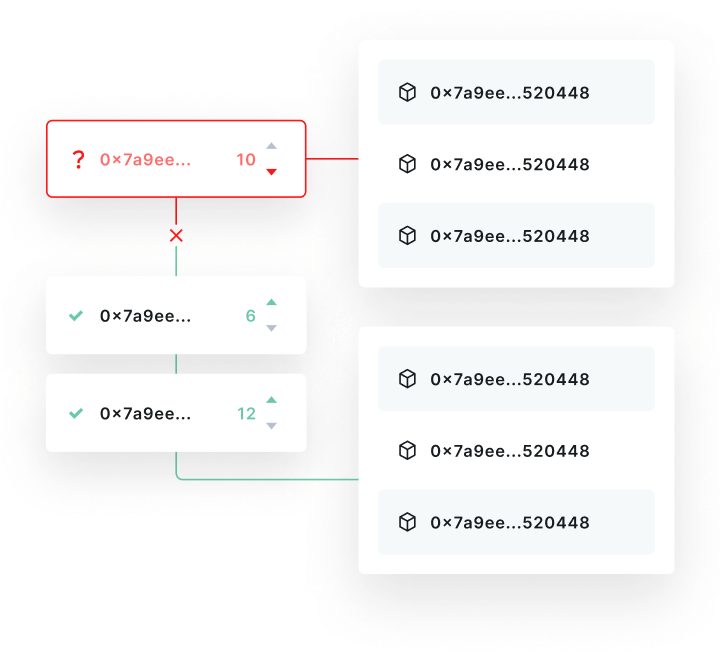
Automated Response System
Instant mitigation protocols that automatically trigger security measures when threats are detected, minimizing response time and potential damage.
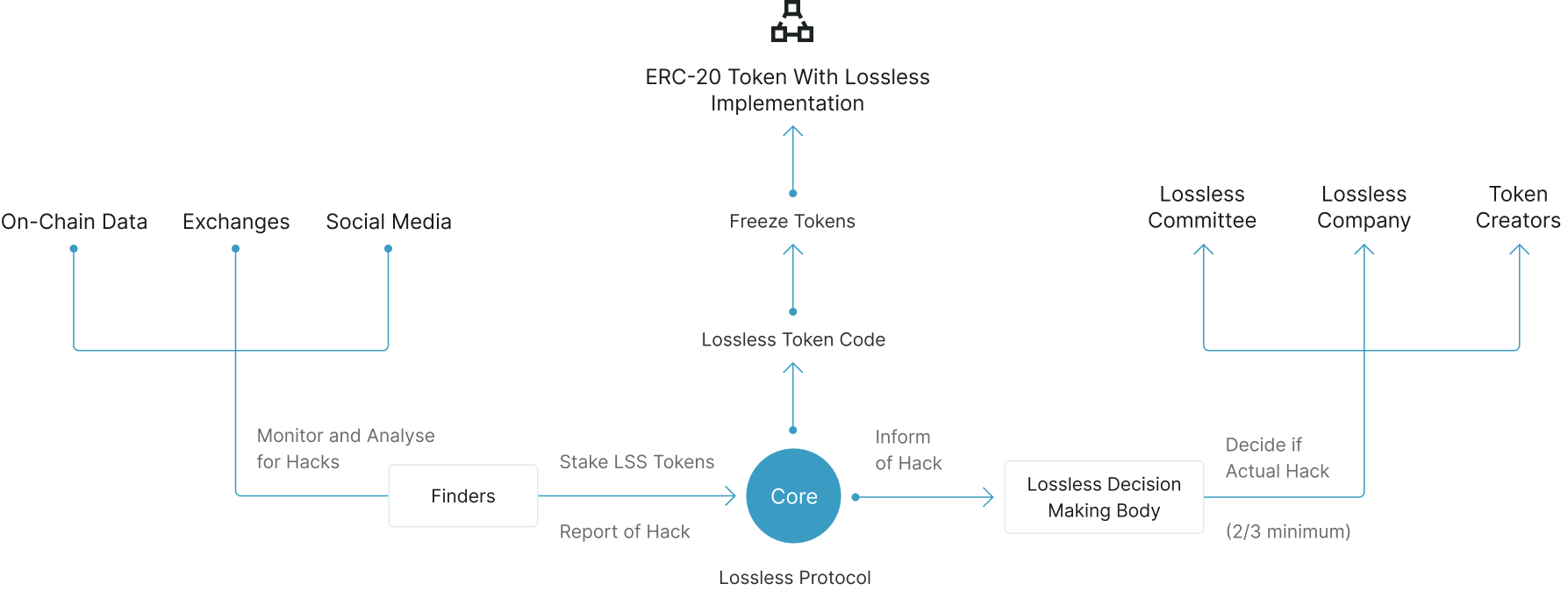
Next-Generation Blockchain Security Technology
Our proprietary technology stack combines quantum-resistant cryptography, zero-knowledge proofs, and distributed consensus mechanisms to create an impenetrable security framework.
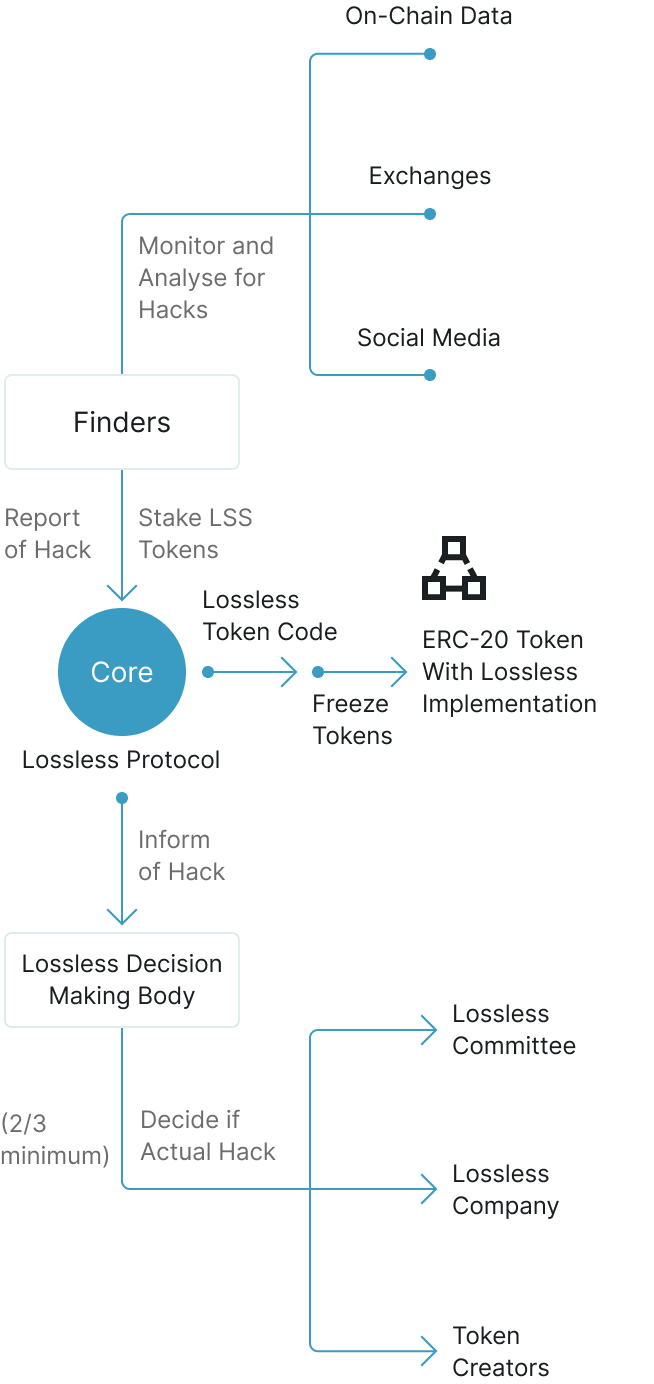

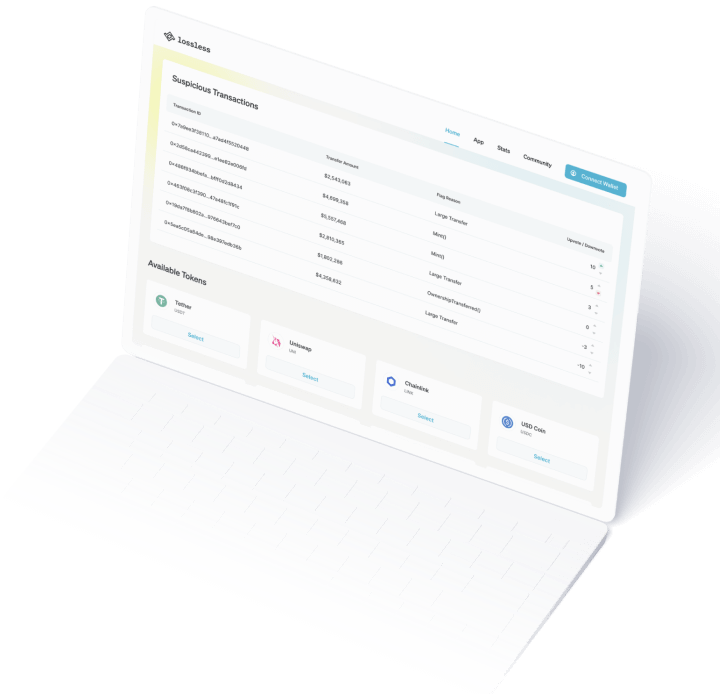
Intuitive Interface for Complete
Crypto Security Management

Real-Time Analytics
Comprehensive dashboard showing live threat intelligence and security metrics

Custom Alerts
Configure personalized notifications for specific security events and threshold breaches
Industry Recognition
Strategic Roadmap 2026
Q1.
-
Quantum-Resistant Encryption Integration
Q2.
-
Cross-Chain Security Protocol
-
AI Threat Intelligence Platform
-
Enterprise API Launch
Q3.
-
Mobile Security Application
-
Regulatory Compliance Module
-
Institutional Partnerships
Q4.

-
Global Expansion Initiative
-
Advanced Predictive Analytics Engine
-
Hardware Integration Solutions
Partners
Customer Feedback
Secure Your Crypto Assets with Enterprise-Grade Protection
Frequently Asked Questions
How does your platform protect against cryptocurrency theft?
Our platform uses multi-layered security including real-time transaction monitoring, behavioral analysis, AI-powered threat detection, and automated response systems. We monitor for suspicious patterns across wallets, exchanges, and smart contracts to prevent unauthorized access and theft.
What blockchain networks do you support?
We support all major blockchain networks including Ethereum, Bitcoin, Binance Smart Chain, Polygon, Solana, Avalanche, and 50+ additional networks. Our system is blockchain-agnostic and can be customized for any emerging blockchain technology.
Is this suitable for individual crypto investors?
Yes, we offer tiered solutions for individual investors, institutional clients, and enterprise organizations. Individual investors benefit from our basic protection plans, while institutions can access advanced features and customized security protocols.
How do you handle smart contract vulnerabilities?
Our platform includes automated smart contract auditing, continuous monitoring for known vulnerabilities, and protection against emerging threats like reentrancy attacks, overflow/underflow, and logic errors. We provide real-time alerts and automatic mitigation measures.
What makes your solution different from traditional security software?
Traditional security software wasn't designed for blockchain technology. Our solution is specifically built for cryptocurrency environments, understanding blockchain-specific threats, decentralized architecture, and the unique security challenges of digital assets.
Do you offer insurance for protected assets?
We partner with leading crypto insurance providers to offer comprehensive coverage options. While our primary goal is prevention, we facilitate insurance solutions for additional protection layers, with coverage amounts tailored to your specific needs and risk profile.
How quickly can threats be detected and neutralized?
Our average threat detection time is under 3 minutes, with automated response systems acting within seconds of detection. We maintain 24/7 security operations with human oversight to ensure rapid response to sophisticated threats requiring manual intervention.